How the Catalog and Coverage Options Work
The Catalog and Coverage options of Coverage Load follow rules to update records and the coverage table with data in the imported file. The rules used by the options are explained below.
Processing Coverage Data with the Catalog Option
NOTE
The Catalog option is available if your library has acquired ERM.
If your library has acquired WebBridge, but not ERM, the Catalog option in Coverage Load is not available.
When you choose the Catalog option in Coverage Load, the system updates your catalog (bibliographic and/or holdings/checkin records) with coverage data from the imported file.
The following diagram illustrates the catalog update process used when you choose the Catalog option.
If your library has acquired ERM, the system creates and updates bibliographic and holdings/checkin records from coverage data as shown here:
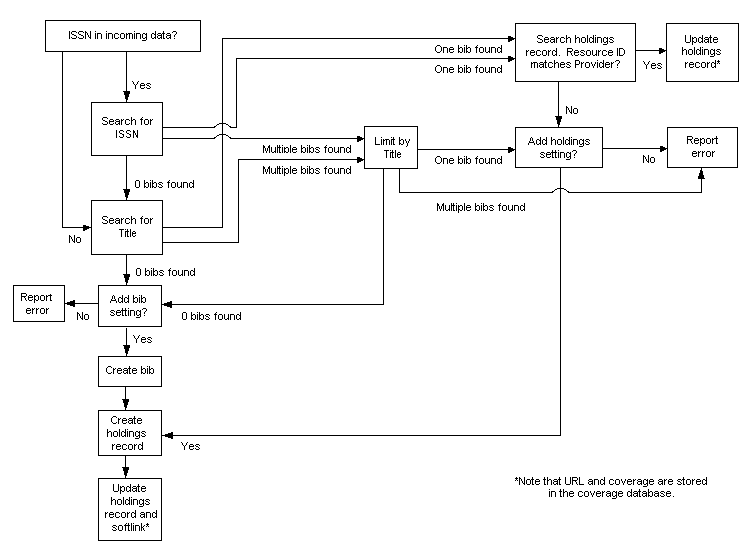
Before attempting to match existing bibliographic records by searching the title index, the system normalizes titles in the coverage spreadsheet according to these rules:
- lowercase all characters
- remove all apostrophes
- remove the articles "a," "an," and "the"
- replace all ampersands with "and"
- replace all other punctuation with a single space
- replace multiple spaces with a single space
- replace subfield delimiters with a space
- stop indexing at the following sequence of characters: "space slash space"
Processing Coverage Data with the Coverage Option
NOTE
The Coverage option in Coverage Load is available if your library has acquired one of the following combinations of products:
- ERM
- Administration and WebBridge
When you choose the Coverage option in Coverage Load, the system updates your coverage table with coverage data from the imported file.
The following table illustrates the coverage update process used when you choose the Coverage option:
| Scenario | System Behavior | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| A single entry in the input file and a single entry in the database | The system replaces all unprotected fields in the database with the corresponding fields in the input file. | ||||||||
| Multiple entries in the input file and a single entry in the database |
|
||||||||
| A single entry in the input file and multiple entries in the database. |
|
||||||||
| Multiple entries in the input file and multiple entries in the database | The first input file entry updates the database entry with the earliest date range. Subsequent updates are in date-range order until all entries are updated.
Additional input file entries are added to the database. If there are more database entries than input file entries, the additional database entries are deleted. |
||||||||
| There are no database entries and a single entry in the input file. | The entry is inserted into the database with all input fields. | ||||||||
| There are no database entries and multiple entries in the input file. | All input entries are added to the database with all input fields. |